
Hackers utilize an unique approach including RBAC (Role-Based Gain Access To Control) to develop consistent backdoor accounts on Kubernetes clusters and pirate their resources for Monero crypto-mining.
RBAC is a Kubernetes API gain access to control system permitting admins to specify which users or service accounts can access API resources and operations.
By abusing RBAC to implement destructive gain access to control policies, hazard stars can continue on jeopardized clusters even if the misconfiguration that supplied preliminary gain access to is repaired in the future.
This brand-new kind of attack was found by Aqua Security‘s research study group, “Nautilus,” who called the project ‘RBAC Buster.’
The experts report that the attack project was observed to be actively utilized to jeopardize 60 misconfigured Kubernetes clusters.
RBAC Buster
Aqua Security might tape and evaluate the attack after the hazard stars breached among its Kubernetes honeypots that were intentionally misconfigured to expose APIs and gain access to secrets.
The preliminary access to the target Kubernetes cluster is accomplished through unauthenticated demands from confidential users with benefits, so the API server requires to be misconfigured.
Next, the assaulter sends out HTTP demands to list tricks and makes API demands to collect details about the cluster by noting entities in the ‘kube-system’ namespace.
At this phase, the assaulter checks if the server was jeopardized currently by their project, released as ‘kube-controller,’ or if other cybercrime rivals have actually currently jeopardized the cluster. If it discovers other assailants’ implementations, it will erase them to take control of the gadget’s resources for its own destructive usage.
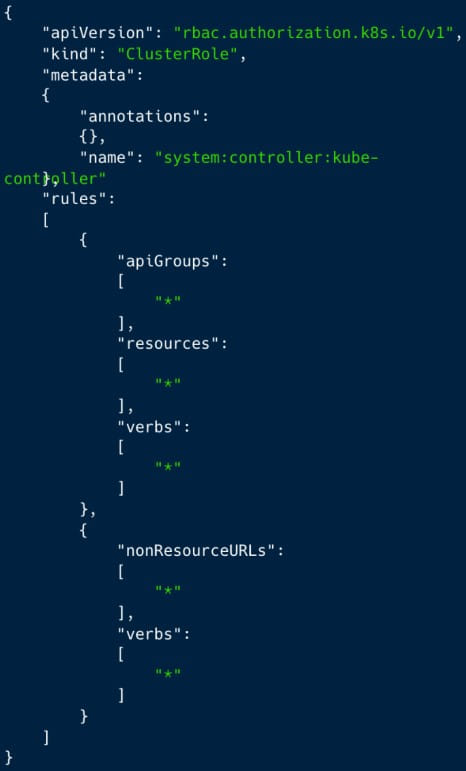
The next action is when the assaulter gains determination on the cluster by producing a brand-new ‘ClusterRole’ with near admin-level benefits and a ServiceAccount ‘kube-controller’ in the ‘kube-system’ namespace.
Lastly, the assaulter develops a ClusterRoleBinding called ‘system: controller: kube-controller,’ binding the ClusterRole with the ServiceAccount to continue the cluster even in the event that ‘confidential user gain access to’ is handicapped.
A ClusterRoleBinding called ‘kube-controller’ was utilized to avert detection and mix into logs, as this name resembles a genuine daemon utilized by Kubernetes.
( AquaSec)
AquaSec’s honeypot intentionally exposed AWS gain access to secrets, and the security company observed that the assailants leveraged them to attempt and collect extra details from the cloud circumstances they might access.
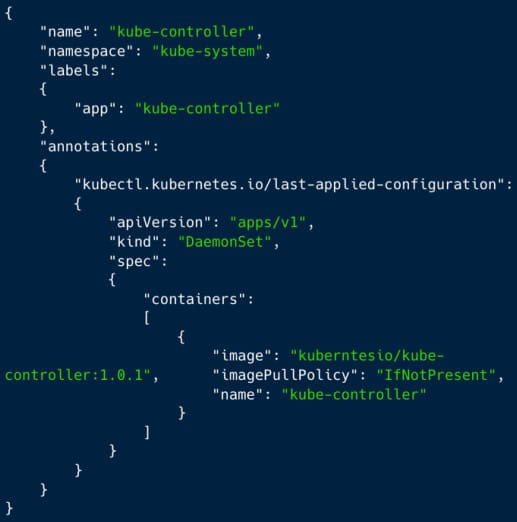
The last action of the attack is to develop a DaemonSet to release a Docker Hub-hosted container image (‘ kuberntesio/kube-controller’) on all nodes with a single API demand and begin mining the hard-to-trace cryptocurrency Monero on the jeopardized server.
Released through typosquatting
Aqua Security discovered that the destructive ‘kube-controller’ container was released from and situated on the general public Docker computer system registry as ‘kuberntesio/kube-controller:1.0.1.’ This name impersonates the genuine ‘kubernetesio’ account and the popular ‘kube-controller-manager’ image.
The latter is a continuously-running vital part of the Kubernetes manage airplane accountable for identifying and reacting to node failures, so it is simple for administrators to neglect.
AquaSec reports that the specific container image has actually been pulled over 14,000 times from Docker Center throughout the 5 months because it was very first submitted to the repository, showing that the project is extensive.
Obtaining the wallet address from the setup file exposed that the assaulter had actually currently mined 5 XMR and has the possible to make the equivalent of $200 per employee annually.
The consequences of the RBAC Buster attacks on Kubernetes clusters can be substantial and consist of unapproved access to information, direct exposure of tricks, resource hijacking, and possibly even track record damage.
To reduce the hazard, protect the API server by prohibiting unauthenticated demands from confidential users and develop and implement stringent API gain access to policies by utilizing RBAC successfully.
Admins are likewise prompted to keep track of audit logs and secure any tricks and account qualifications hosted in the cluster.