In context: The e-file system is the internal revenue service’ formally authorized format for sending tax documents through the web, normally without any requirement to offer any paper file. Netizens can utilize software application or sites to send their income tax return, despite the fact that utilizing external services can cause extra security threats.
Tax Day for United States residents is approaching quickly, and cyber-criminals are making use of the April 18 due date to increase their harmful projects versus users and legitimate tax-filing services. The eFile.com online platform just recently got captured in this tax-related cybercrime revival, ending up being a (most likely) uninformed spreader of harmful JavaScript files and malware payloads.
As reported by Bleeping Computer system and verified by various security scientists, nearly every page of the eFile site was serving a destructive JS script called “popper.js” a minimum of up until April 1st. The base64-encoded script was developed to fill extra JS code from the infoamanewonliag dot online domain, which in turn would trigger users to download the real malware payload called “update.exe” (for Chrome web browsers) or “installer.exe” (Firefox).
Scientist verified that the executable binaries consisted of a Windows backdoor composed in PHP, developed to develop a connection with a Tokyo-based IP address (47.245.6.91) hosted by Alibaba. The exact same IP was likewise hosting the infoamanewonliag domain pinged by the popper.js harmful script.
As soon as carried out, the backdoor-carrying binary would run in the background, patiently waiting on orders originating from remote servers. The PHP script would link to a command&& nerve center every 10 seconds, and it might perform hazardous jobs like running a regional command to send out the output to the server, or downloading extra files on the jeopardized PC.
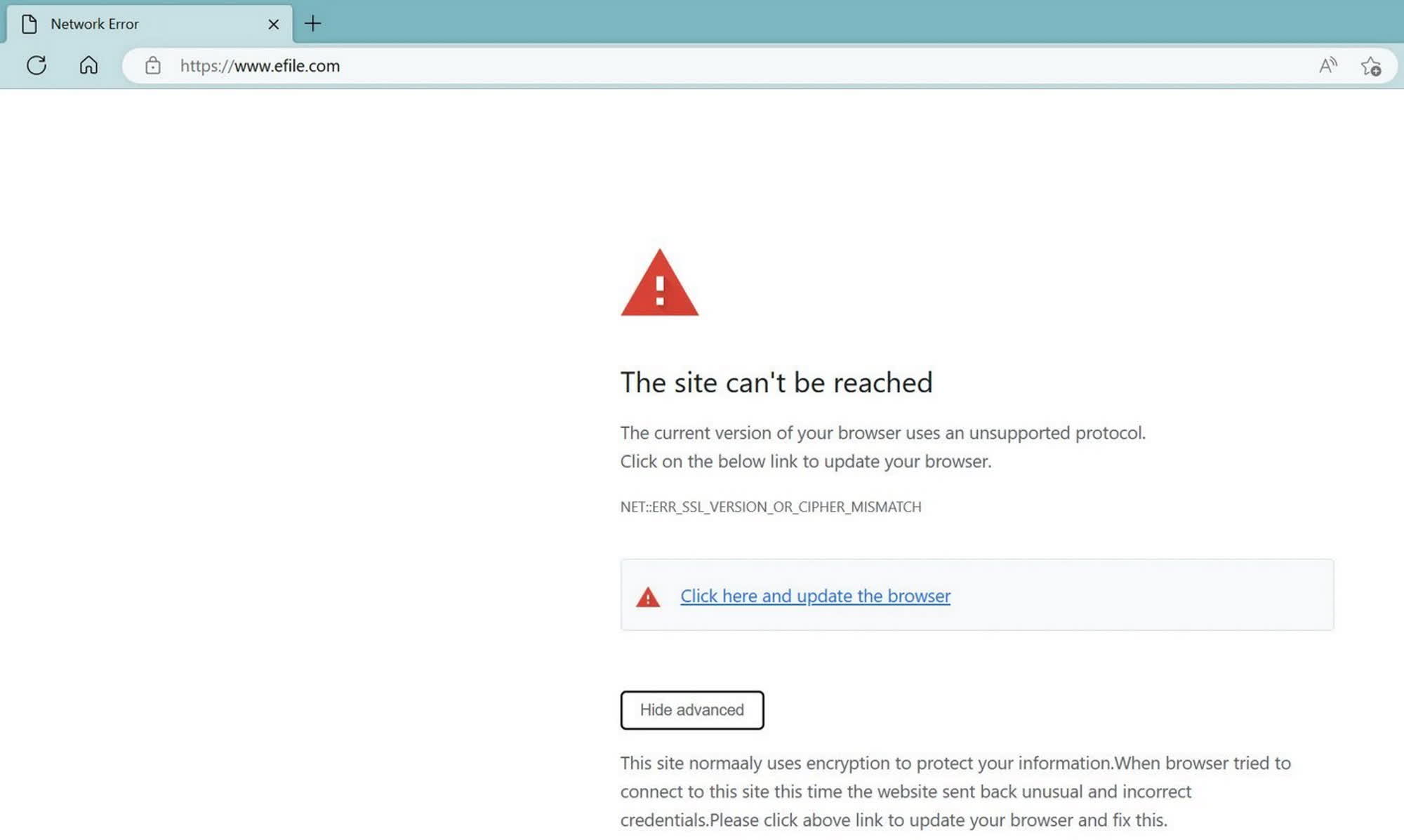
The backdoor-serving infection of eFile.com was apparently currently active in March, when a Reddit thread highlighted a perhaps phony SSL mistake returned by the HTTPS-enabled site. The phony mistake was served by a destructive file called “update.js,” which was developed to trigger users to download the previously mentioned backdoored binary files update.exe and installer.exe.
While supplying simply the fundamental functions for this type of harmful software application, the eFile backdoor threatened sufficient to provide cyber-criminals complete access to a contaminated Windows PC and more utilize to assault other systems in a business network. The eFile.com business still needs to offer any description about the event, while the cyber-gang behind the LockBit ransomware was declaring that they effectively assaulted the site in January 2022 currently.